The recent drafts from National Institute of Standards and Technology (NIST) around cybersecurity highlight important updates on where the government is moving on technology and the focus on increasing security against cyber threats. This is because NIST’s primary goal is to develop and disseminate the standards that allow technology to work seamlessly and businesses to operate smoothly. In December 2022, NIST provided an update to NIST special publication 800-63-4 ipd (initial public draft), which details Digital Identity Guidelines designed to help strengthen digital identity assurance and authentication, recognizing shifts in both risk and emerging authentication models such as phishing-resistant multi-factor authentication (MFA) and passkeys.
The details of the draft guidelines are important because they affect agency operations at large. 800-63-4 ipd clearly defines what it means to be phishing-resistant, and it comes at a time when many government agencies (especially state and local governments) are besieged by phishing attacks and ransomware demands. However, it’s important to understand what phishing-resistance authentication means for federal, state and local agencies, and what needs to be done to abide by these proposed guidelines.
What does phishing-resistance mean for me and my agency?
As with all federal guidelines and legislation, NIST guidelines will continue to evolve – but federal agencies have been put on notice by 800-63-4 ipd that they should pay close attention to what counts as phishing-resistant technology: “the ability of the authentication protocol to detect and prevent disclosure of authentication secrets and valid authenticator outputs to an impostor relying party without reliance on the vigilance of the subscriber.” At a high level, authentication systems need to prevent phishing attacks even if the attacker can trick a user to try and log into a fake site. Deadlines for compliance – for agencies and the companies that work with them – will be coming up fast, so it’s worth going through 800-63-4 ipd to parse what is most relevant for near-term upgrade plans.
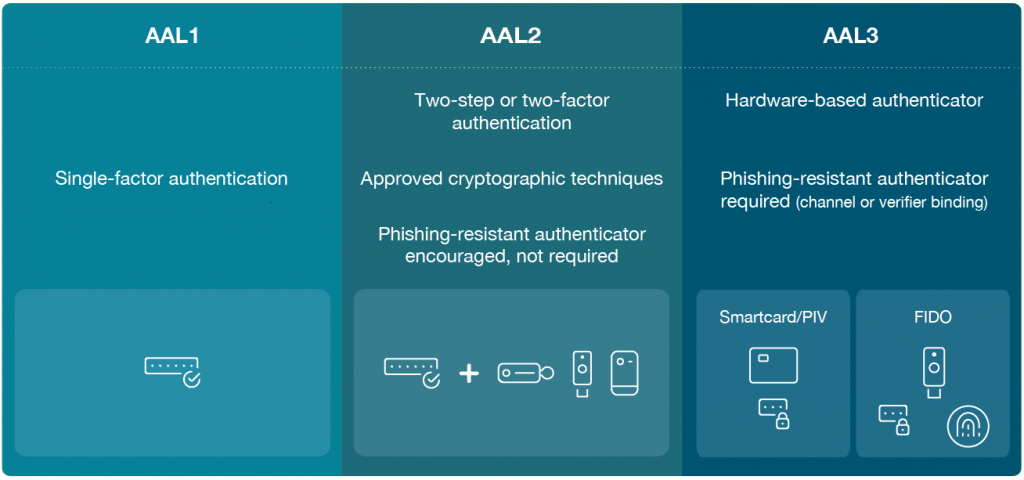
The NIST guidelines are designed to help strengthen digital identity assurance and authentication, recognizing shifts in both risk and emerging authentication models such as passkeys. There are three authentication assurance levels (AALs) identified, with each level building on the previous level’s requirements. AAL3 provides very high confidence that someone logging onto your system can, by proof of possession, prove they are who they are claiming to be. FIPS validated authenticators for federal workers are required for AAL2 (level 1) and AAL3 (level 2).
The revised NIST guidelines also recognize two methods of phishing-resistant authentication: channel binding and verifier name binding. In plain language, the methods are designed to prevent an imposter from successfully hijacking or intercepting the authentication process.
Channel binding refers to the communication channel between the authenticator (such as a smart card) and the verifier. On traditional networks this communication is protected by the encrypted channel so nobody is able to listen in. This is not the case on the web so standard web communication is not protected enough unless mutual/client authenticated TLS is used, which is the reason verifier name binding method was introduced which the FIDO2 standard leverages. In verifier name binding, the authentication process will only respond to the previously registered domain name. Both methods are resistant to attempts to compromise or subvert the authentication process.
So when is it all happening? It will be a process, but government agencies, already bound by the FIPS 140 standard, are required by the end of FY2024 to adopt exclusive use of phishing-resistant multi-factor authentication (MFA). The minimum standard will be the AAL2 level, but note that certain legacy authentication processes like SMS-based “one-time-passwords” OTP will not meet the new standards for phishing resistance. Some companies may choose to leapfrog AAL2 completely and move to AAL3 to get the highest assurance defense against phishing attacks.
How will this impact what I am using today?
800-630-4 ipd says true phishing resistance is only achieved when all methods of authentication are phishing-resistant. PIV/CAC smart cards support phishing-resistant MFA but in cases where PIV/CAC cannot be used, then those authentication mechanisms must move to a phishing-resistant method like FIDO2.
At the start of 2023, NIST continued a series of updates it has instituted for PIV with its Guidelines for Derived PIV Credentials (SP 800-157r1) and new Guidelines for Personal Identity Verification (PIV) Federation (SP 800-217). The updates are NIST’s way of integrating new methods with established authentication approaches.These guidelines will hopefully provide clarity on how to successfully implement FIDO2 and federation for agencies.
Agencies can implement FIDO2 solutions strategically to cloud and mobile based applications, while continuing to utilize their existing PKI investment on traditional networks. With time they can expand FIDO2’s footprint to include other use cases, such as application login, computer logon, and remote logon.
Don’t swim against the current, let it take you to a safer place
The confluence of President Biden’s new cyberstrategy and the draft SP 800-63-4 ipd publication is a good signal for all of us looking to protect what we have – whether that is PII data, agency “crown-jewel” data or communications with third parties.
FIDO2 authentication is an essential part of a larger, flexible, phishing-resistant infrastructure now being developed. FIDO2 and PKI solutions are made to complement each other rather than live in an “either-or” world. Phishing-resistant AAL3 solutions are available today and are being more widely adopted. If federal agencies swim with the current rather than against it, they will strengthen their defenses and curtail phishing attacks dramatically.
——
This is part 1 of a two-part series on the new NIST guidance. Stay tuned for a second Q&A post where we’ll dive deeper into the impacts for federal agencies and answer some top questions we’re seeing from customers on the guidance.
*This post was originally published in Federal News Network
——
For more information on modern authentication methods for government, download the Modern Authentication Across Federal Government white paper. To see what you should do to respond to The White House’s National Cybersecurity Strategy and Pandemic Anti-Fraud Proposal, check out our blog here.
The post NIST SP 800-63-4: What the new phishing-resistant definition means for federal agencies appeared first on Yubico.
—————-
VaultumCity is the best trusted place to select and buy your best Yubikeys, Vaultumcity free ship all yubikeys, Vaultumcity is reseller distributor of yubikeys so you can find cheapest best yubikey in Vaultumcity. If you are looking for best Yubikeys in Singapore at VaultumCity website online store.
The shop that sells yubikeys is https://vaultumcity.com/product-category/yubikey/
Our delivers are from Singapore, distribute globally. Buying Yubikey in Vaultum to have best customer and after sales services. All Yubikeys sold at Vaultumcity are quality guaranteed. Please place a large amount order to have great discount for reseller. Contact Vaultumcity at https://vaultumcity.com/contact/ whenever you have any issue with your yubikeys. Buying yubikeys at Vaultumcity to have best newest yubikeys free shipped to your door, FIDO2 U2F SECURITY KEY C NFC, FIDO2 U2F SECURITY KEY NFC, YubiKey 5 Nano, YUBIKEY 5 NFC, YubiKey 5C, YubiKey 5C nano, YubiKey 5C NFC, YUBIKEY 5Ci, YubiKey Bio – FIDO Edition. Yubikeys are best most secure tools for two-factor authentication. You can also buy yubikeys form Malaysia, Yubikey Malaysia is being sold at Vaultumcity with great price and free ship, you have it fastest, just in few days because we’re here in Singapore.
If you are looking for yubikeys in Indonesia, Vaultumcity is a great place to buy yubikey Indonesia, you can have yubikeys to protect your logins in just few days. Vaultumcity ship your yubikeys to your home in Thailand, to help ensure your data is safe and secured.
What about South Korea, Vaultumcity bring your yubikeys to your home in South Korea free-shipped.
Vaultumcity also delivers yubikeys to Japan, any province or city to your hands. Check out and grab your best suited yubikey today at VaultumCity.